Advanced Penetration Testing for Highly-Secured Environments
English | MP4 | 1280×720 | AVC 172 Kbps 30.000 fps | AAC 48.0 Kbps 48.0 khz | 3 hours | 717 MB
Advanced Penetration Testing for Highly-Secured Environments will teach you how to effectively secure any environment and harden your system and network configurations. You will be able to get into the attacker’s mindset of how they target systems on a network and the overwhelming threats they pose, thereby exploiting their vulnerabilities to create a step-by-step virtual lab to protect your system.”
Section 1: Introduction to Advanced Penetration Testing
Lecture 1
What Is Advanced Penetration Testing?
03:43
Ever wondered how hackers got into your system or network? Throughout this video course, you will learn advanced techniques on how hackers get into systems and networks. This is very important to know because security awareness can help prevent these attacks.Lecture 2
Installing VirtualBox
04:42
Learn how to install VirtualBox on Windows 7.Lecture 3
Installing BackTrack 5 R3
04:25
Learn how to install BackTrack 5 R3 in VirtualBox on Windows 7.Lecture 4
Installing Metasploitable
02:47
Learn how to install Metasploitable in VirtualBox on Windows 7.Lecture 5
Set up BackTrack 5 R3
04:12
Learn how to set up and configure BackTrack 5 R3.Section 2: Advanced Footprinting
Lecture 6
What Is Footprinting?
03:05
Learn what footprinting is, the methods, and also the usage of the tools.Lecture 7
Using Nslookup and Dig
04:13
Learn how to use Nslookup and Dig commands in Windows and Linux.Lecture 8
Using Tracert and Traceroute
04:35
Learn how to use the Tracert and Traceroute commands in Windows and Linux.Lecture 9
Using Paterva Maltego
04:47
Learn how to use Paterva Maltego in BackTrack Linux.Lecture 10
Google Dorks and Social Engineering
05:16
This video will explain what Google Dorks and Social Engineering is with a few examples.Section 3: Enumeration: Getting to Know Your Target
Lecture 11
What Is Enumeration?
02:32
Enumeration is where you gather information, such as usernames, groups, network shares, services running on the network, and the number of hosts.Lecture 12
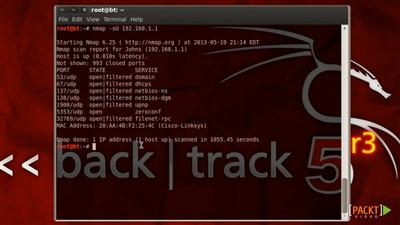
Using Nmap and Zenmap
06:07
In this video, you will learn how to use Nmap and Zenmap to scan hosts.Lecture 13
Using SNMPenu and SNMPwalk
04:51
In this video, you will learn how to use SNMPenu and SNMPwalk.Lecture 14
Banner Grabbing with Netcat
Preview
03:36
Banner grabbing allows you to grab more information from a website, such as the service name and version.Lecture 15
Searching for Exploits
03:30
Ever wondered how hackers found exploits? In this video, we will be searching for exploits.Section 4: Exploitation Applications: Getting to Know Your Tools
Lecture 16
What Is Exploitation?
04:18
Exploitation is where you trick a user or system into getting compromised. You can trick a user through social engineering techniques and you can trick a system into running arbitary code.Lecture 17
Installing the Nessus Vulnerability Scanner
04:21
In this video, you will learn how to install and configure the Nessus Vulnerability Scanner.Lecture 18
Using the Nessus Vulnerability Scanner-Part 1
Preview
04:52
In this video, you will learn how to scan a system for a list of vulnerabilities. This can help identify exploits that could affect your system.Lecture 19
Installing and Updating the Metasploit Framework
02:57
Always keep the Metasploit Framework up to date with the latest exploits and payloads.Lecture 20
Using the Metasploit Framework
07:32
Using the Metasploit Framework can help with security awareness. It helps keep the user aware of what is out there that could affect their system or network.Section 5: Gaining Physical Access
Lecture 21
How Do Hackers Break into a Local System?
03:27
Every day there is always someone talking about their computer or online accounts getting hacked. This video could help stop it from happening to you.Lecture 22
Breaking into Windows 7-Part 1
Preview
02:48
KON BOOT is a live cd that can bypass passwords just by booting them from the disk. To fix this issue, encrypt your hard drive and use strong complex passwords.Lecture 23
Breaking into Windows 7-Part 2
03:00
Use the Ubuntu Live CD to bypass a Windows partition and copy files and delete files. To fix this issue, encrypt your hard drive.Lecture 24
Breaking into Windows 7-Part 3
04:31
Use the Ubuntu Live CD to replace some system files to trick Windows into opening Command Prompt instead of the Sticky Keys dialog box.Lecture 25
Breaking into Windows 7-Part 4
02:28
Ophcrack allows you to crack Windows SAM files on the fly. To fix this issue, encrypt your hard drive and use strong complex passwords.Section 6: Exploiting a Client-side Target
Lecture 26
How Do Hackers Break into a Remote System?
05:27
Every day there is always someone talking about their computer or online accounts getting hacked. This video could help stop it from happening to you.Lecture 27
Using the Social Engineering Toolkit
04:00
The Social Engineering Toolkit has many different features to exploit an individual. When a pen-tester can’t access the system, they try exploiting the user.Lecture 28
Using the Nessus Vulnerability Scanner-Part 2
Preview
05:14
Nessus Vulnerability Scanner is one of the best ways to determine if your system is vulnerable to the Internet. Learning to use Nessus is essential for keeping your system safe from hackers.Lecture 29
Exploiting Windows 7
05:04
Most business and home users still use Windows XP and 7. What they don’t know could potentially leave them at risk in a compromised system and accounts.Lecture 30
Exploiting Metasploitable
05:42
This is a great way to test out exploits on your own without running into any legal matters. This helps improve security awareness for the user and helps understand how important it is to keep your system up to date with the newest technologies.Section 7: Bypassing Web Filters, Firewalls, and IDS
Lecture 31
Evading Web Filters, Firewalls, and IDSes
05:38
Ever wondered how companies get compromised and their accounts get hacked? This video teaches you how hackers break into web filters, firewalls, and IDSes.Lecture 32
Bypassing Web Filters-Part 1
05:21
Wondered how your staff or students bypassed the web restrictions on the computer? Learn how to use proxies to re-route your traffic to another server.Lecture 33
Bypassing Web Filters-Part 2
03:39
Still can’t bypass that annoying web filter? Learn how to use a VPN to re-route your traffic over an encrypted network.Lecture 34
Stealth Scanning-Part 1
Preview
02:32
Learn how to use Nmap to stealth scan a target host.Lecture 35
Stealth Scanning-Part 2
04:49
Learn how to use Zenmap to stealth scan a target host.Section 8: Writing a Penetration Testing Report
Lecture 36
Why Is It So Important to Write a Report?
Preview
04:28
You are done pen-testing the network; now what? You need to write a professional penetration testing report for your client to prove to them what vulnerabilities and exploits are available for their network.Lecture 37
What Should Be In the Report?
03:55
Its always good to know what to put in your report before handing it to your client for review.Lecture 38
Writing a Report
04:43
Now that you know why it’s important to write a report, it’s time to write a report. In this video, you will see an example of what a written report should look like when being handed to a client for review.Lecture 39
Turning In the Report
03:14
Finally, you can hand in your report to your client. Make sure you have every detail listed; don’t forget any vulnerabilities or exploits.Lecture 40
Final Statement by the Author
04:26
Recommendations given by the authorGeneral
Complete name : Advanced Penetration Testing for Highly-Secured Environments\1.1.MP4
Format
: MPEG-4
Format profile : Base Media
Codec ID
: isom
File size
: 5.93 MiB
Duration
: 3mn 43s
Overall bit rate mode : Variable
Overall bit rate : 222 Kbps
Encoded date : UTC 2014-10-24 12:47:05
Tagged date
: UTC 2014-10-24 12:47:05Video
ID : 1
Format
: AVC
Format/Info
: Advanced Video Codec
Format settings, CABAC : No
Format settings, ReFrames : 3 frames
Codec ID
: avc1
Codec ID/Info : Advanced Video Coding
Duration
: 3mn 43s
Bit rate
: 172 Kbps
Maximum bit rate : 933 Kbps
Width
: 1 280 pixels
Height
: 720 pixels
Display aspect ratio : 16:9
Frame rate mode : Constant
Frame rate
: 30.000 fps
Color space
: YUV
Chroma subsampling: 4:2:0
Bit depth
: 8 bits
Scan type
: Progressive
Bits/(Pixel*Frame): 0.006
Stream size
: 4.59 MiB (77%)
Writing library : Zencoder Video Encoding System
Encoded date : UTC 2014-10-24 12:45:18
Tagged date
: UTC 2014-10-24 12:47:06
Color primaries : BT.709
Transfer characteristics : BT.709
Matrix coefficients: BT.709
Audio
ID : 2
Format
: AAC
Format/Info
: Advanced Audio Codec
Format profile : LC
Codec ID
: 40
Duration
: 3mn 43s
Bit rate mode : Variable
Bit rate
: 48.0 Kbps
Maximum bit rate : 63.6 Kbps
Channel(s)
: 2 channels
Channel positions: Front: L R
Sampling rate : 48.0 KHz
Compression mode : Lossy
Stream size
: 1.27 MiB (21%)
Encoded date : UTC 2014-10-24 12:47:05
Tagged date
: UTC 2014-10-24 12:47:06
Download From RapidGator
http://rapidgator.net/file/dd2392ff5a72485b71e054d18a4c46d2/ig040.A.P.T.f.HS.E.part1.rar.html http://rapidgator.net/file/ab6a76f888cfdb10372634ffc65b9766/ig040.A.P.T.f.HS.E.part2.rar.html http://rapidgator.net/file/bb588ded3d5737fe8b08a2cf144e3ed0/ig040.A.P.T.f.HS.E.part3.rar.html
Download From SecureUpload
http://www.secureupload.eu/cha6ktfl860w/ig040.A.P.T.f.HS.E.part1.rar http://www.secureupload.eu/vg4oqnl1xir5/ig040.A.P.T.f.HS.E.part2.rar http://www.secureupload.eu/t4qezvs64wex/ig040.A.P.T.f.HS.E.part3.rar